UofT CTF Writeup
Secret Message 1
Challenge
We swiped a top-secret file from the vaults of a very secret organization, but all the juicy details are craftily concealed. Can you help me uncover them?
Attachment: A pdf file which has a redacted text.
Solution
Using a simple online tool that converts pdf to text gives out the flag. First result from Google: https://www.pdf2go.com/pdf-to-text
uoftctf{fired_for_leaking_secrets_in_a_pdf}
Out of the Bucket
Challenge
Check out my flag website!
Attachment: A Google bucket link
Solution
If we shorten the URL to https://storage.googleapis.com/out-of-the-bucket/, we get an XML file containing the structure and the content of this bucket.
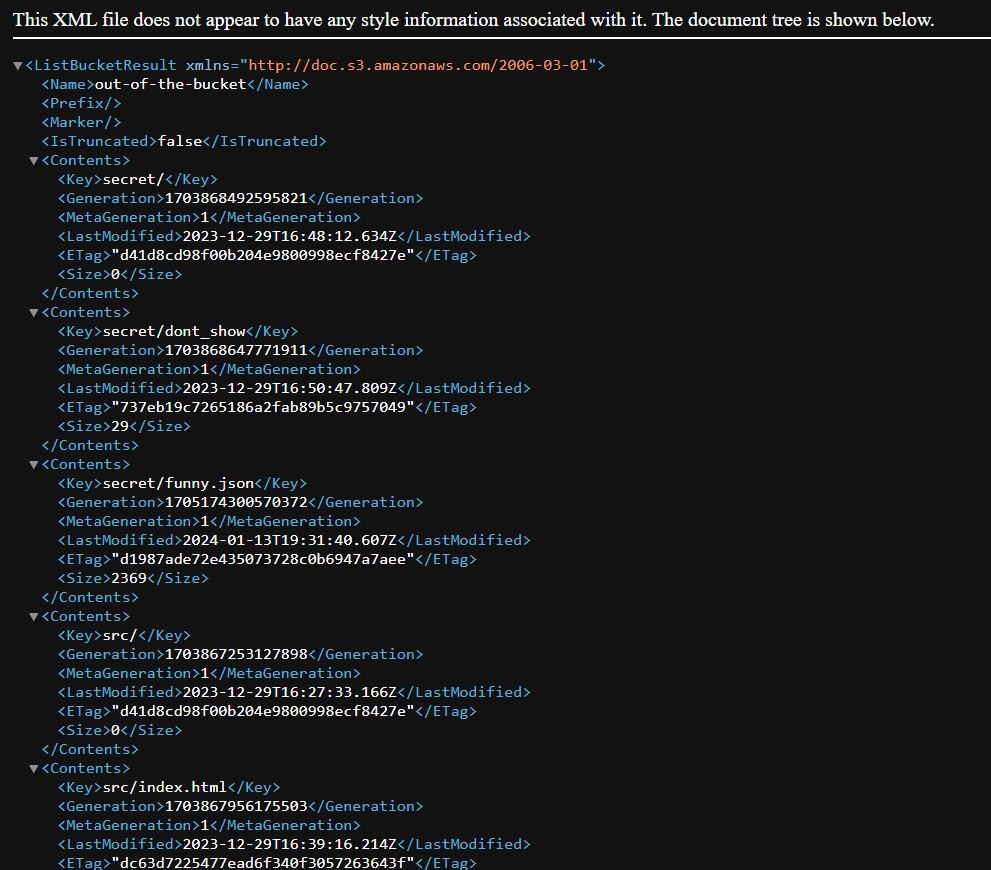
Going to /secret/dont_show will download a file which has the flag:
uoftctf{allUsers_is_not_safe}
Out of the Bucket 2
Challenge
This is a continuation of "Out of the Bucket". Take a look around and see if you find anything!
Solution
From the above screenshot, there is another interesting thing to look at, which is the way for this challenge: /secret/funny.json:
{ "type": "service_account", "project_id": "out-of-the-bucket", "private_key_id": "21e0c4c5ef71d9df424d40eed4042ffc2e0af224", "private_key": "-----BEGIN PRIVATE KEY-----\nMIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQDWxpWEDNiWgMzz\nxDDF64CspqiGPxkrHfhS4/PX8BrxNjUMPAH7vYHE3KbgQsmPhbCte9opnSLdMqec\nWjll8lRZGEy73xhWd2e3tVRAf53r+pW/p6MTOsz3leUkQAscG4hmOVOpGb1AkfuE\n62NErJVZIgQCowrBdFGbPxQc/IRQJKzrCFfKOWSHLvnngr4Ui5CSr6OM33dfpD+v\nQSLkEQheYCXmHwh/Wf8b27be+RzfOp/hOyjKsJOmDvFu2+rrx24t8hCptof3BYol\nUjpaiB8Qcct/HoKOEvZ/S5rW6toQizP8t4t7urC2i70JdH+Y4Qw/AZJNuLo/5wW1\n+x8i3FIDAgMBAAECggEABaGapVC06RVNdQ1tffL+d7MS8296GHWmX34B6bqDlP7S\nhenuNLczoiwVkAcQQ9wXKs/22Lp5rIpkd1FXn0MAT9RhnAIYdZlB4JY3iaK5oEin\nXn67Dt5Ze3BfBq6ghpx43L1KDUKogfs8jgVMoANVEyDfhrYsVQWDZ5T60QZp7bP2\n0zSDSACZpFzdf1vXzOhero8ykwM3keQiCIKWYkeMGsX8oHyWr1fz7AkU+pLciV67\nek10ItJUV70n2C65FgrW2Z1TpPKlpNEm8jQLSax9Bi89HuFEw8UjTfxKKzhLFXEu\nudtAyebt/PC4HS9FLBioo3bAy8vL3o00b7+raVyJQQKBgQD3IWaD5q5s7H0r10S/\n7IUhP1TDYhbLh7pupbzDGzu9wCFCMItwTEm9nYVNToKwV+YpeyoptEHQa4CAVp21\nO4+W7mBQgYemimjTtx1bIW8qzdQ9+ltQXyFAxj6m3KcuAsAzSpcHkbP46lCL5QoT\nTS6T06Fs4xvnTKtBdPeisSgiIwKBgQDee+mp5gsk8ynnp6fx0/liuO3AZxpTYcP8\nixaXLQI6CI4jQP2+P+FWNCTmEJxMaddXNOmmTaKu25S2H0KKMiQkQPuwBqskck3J\npVTHudnUuZAZWE7YPg40MJgg5OQhMVwiqGWL76FT2bubIdNm4LQyxvDeK82XQYl8\nszeOXfJeoQKBgGQqSoXdwwbtF5Lkbr4nnJIsPCvxHvIhskPUs1yVNjKjpBdS28GJ\nej37kaMS1k+pYOWhQSakJCTY3b2m3ccuO/Xd6nXW+mdbJD/jsWdVdtxvjr4MMmSy\nGiVJ9Ozm9G/mt4ZSjkKIIN0cA8ef7uSB3QYXug8LQi0O2z7trM1pZq3nAoGAMPhD\nOSMqRsrC6XtMivzmQmWD5zqKX9oAAmE26rV8bPufFYFjmHGFDq1RhdYYIPWW8Vnz\nJ6ik6ynntKJyyeo5bEVlYJxHJTGHj5+1ZnSwzpK9dearDAu0oqYjhfH7iJbNuc8o\n8sEe2E7vbTjnyBgjcZ26PJyVlvpU4b6stshU5aECgYEA7ZESXuaNV0Er3emHiAz4\noEStvFgzMDi8dILH+PtC3J2EnguVjMy2fceQHxQKP6/DCFlNqf9KUNqJBKVGxRWP\nIM1rcoAmf0sGQ5gl1B1K8PidhOi3dHF0nkYvivuMoj7sEyr9K88y69kdpVJ3J556\nJWqkWLCz8hx+LcQPfDJu0YE=\n-----END PRIVATE KEY-----\n", "client_email": "[email protected]", "client_id": "102040203348783466577", "auth_uri": "https://accounts.google.com/o/oauth2/auth", "token_uri": "https://oauth2.googleapis.com/token", "auth_provider_x509_cert_url": "https://www.googleapis.com/oauth2/v1/certs", "client_x509_cert_url": "https://www.googleapis.com/robot/v1/metadata/x509/image-server%40out-of-the-bucket.iam.gserviceaccount.com", "universe_domain": "googleapis.com" }
This looks like a classic credentials.json file which is created by Google Cloud apps. More importantly, it has a private key, which means it should give us access to this service account. But how?
First, I tried creating a python script to connect to the account's API because this is the usual way. But I couldn't get any interesting info with this method. Then, I tried directly connecting via Google Cloud Shell. I uploaded the json file to the shell environment and entered the following command to get access to the service account:
gcloud auth activate-service-account --project="out-of-the-bucket" --key-file="funny.json"
It successfully activated the account. Now we need to enumerate a lot in order to find the next step. So, in order to see what we can enumerate in this account, we can run the following command:
gcloud services list --enabled
At this point, I spent significant time to find a point to move on. But eventually, I found an interesting thing:
gsutil ls gs://
With the result:
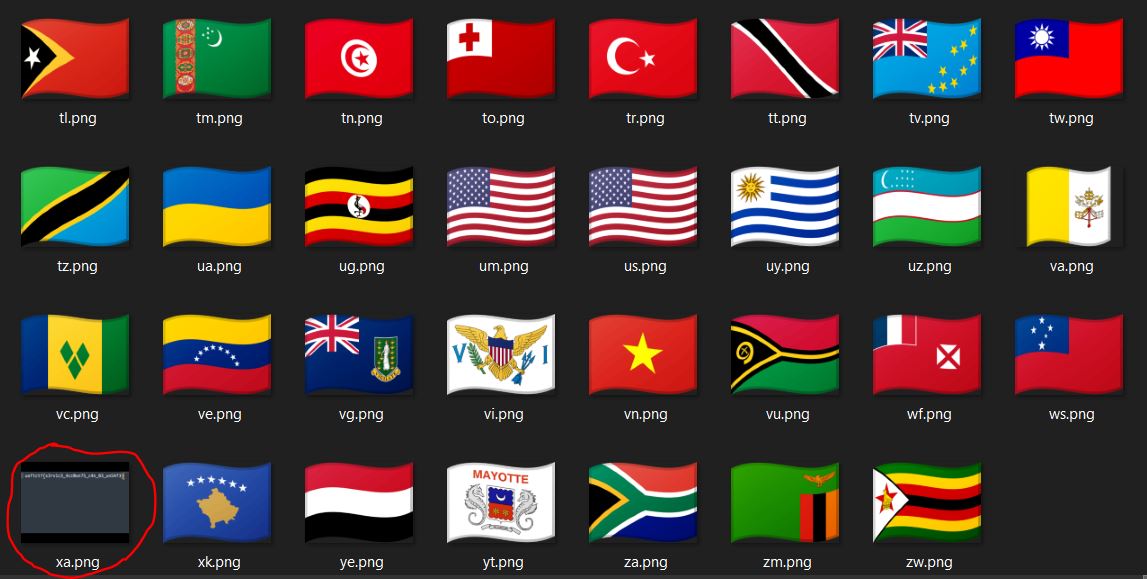
gs://flag-images/ gs://out-of-the-bucket/
Inside flag-images/256x192/ there were a lot of pictures of country flags. There were so many, so it would take too much time to check them one by one. I zipped the folder and downloaded. And here is our flag: